Cyber Security Compliance Assessment
1. Privacy Act 1988: The Privacy Act governs the collection, use, storage, and disclosure of personal information by Australian entities. It includes the Australian Privacy Principles (APPs) that outline requirements for the secure handling of personal data, including implementing appropriate security measures to protect against unauthorized access, disclosure, loss, or misuse.
–
2. Notifiable Data Breaches (NDB) Scheme: The NDB Scheme mandates that organizations covered by the Privacy Act must notify affected individuals and the Office of the Australian Information Commissioner (OAIC) of eligible data breaches that are likely to result in serious harm. Assessing compliance with the NDB Scheme involves evaluating an organization’s incident response procedures, breach notification capabilities, and measures taken to prevent data breaches.
–
3. Australian Government Information Security Manual (ISM): The ISM provides guidance to Australian government agencies on how to protect their information and systems. While it is primarily targeted at government entities, it can also be a useful reference for non-government organizations. Compliance assessments against the ISM involve evaluating an organization’s adherence to the recommended security controls and measures.
–
4. Payment Card Industry Data Security Standard (PCI DSS): If an organization processes, stores, or transmits payment card data, it may need to comply with the PCI DSS. The PCI DSS is a set of requirements for securing payment card data and maintaining a secure payment card environment. Compliance assessments against PCI DSS involve evaluating an organization’s controls and practices related to cardholder data protection.
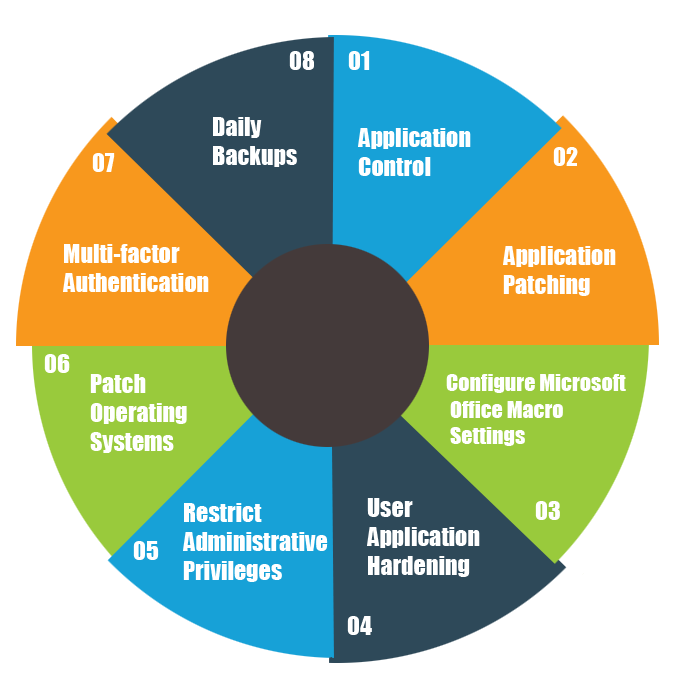
5. Essential Eight: Essential Eight is a set of mitigation strategies developed by the Australian Signals Directorate (ASD) to enhance cyber security resilience against targeted cyber intrusions.
Organizations can assess their compliance with the Essential Eight strategies and maturity levels to determine their level of cyber security readiness.
When conducting a compliance assessment in Australia, organizations should consider engaging with cyber security professionals or consultants with expertise in the applicable regulations and frameworks to ensure a thorough and accurate evaluation. It is important to stay up to date with the latest legal and regulatory requirements as they may evolve over time.